Deploy Infisical Through Docker
Introduction
Infisical is an open-source platform to manage secrets and configs across your team and infrastructure. I liked it because it looks much more user friendly than Vault, although Vault is a lot more powerful with more features, but more complexity.
Caveats
Proxy Required
This deployment requires that you have your own proxy for managing and terminating TLS connections.
No PHP SDK (currently)
There is no official PHP SDK, but I intend to create and publish my own package to handle this.
Shared Secrets Do Not Exist
Unfortunately, shared secrets between projects do not exist. E.g. if you have one set of SMTP credentials that get used between different services, with each service being its own project, one has to have those SMTP credentials repeated in each of the projects: https://github.com/Infisical/infisical/issues/1049
Steps
Create Docker Compose File
services:
db-migration:
image: infisical/infisical:${INFISCAL_VERSION:-v0.63.1-postgres}
container_name: infisical-db-migration
pull_policy: always
command: npm run migration:latest
depends_on:
db:
condition: service_healthy
environment:
- NODE_ENV=production
- ENCRYPTION_KEY
- AUTH_SECRET
- SITE_URL
- DB_CONNECTION_URI=postgres://${POSTGRES_USER}:${POSTGRES_PASSWORD}@db:5432/${POSTGRES_DB}
- REDIS_URL=redis://redis:6379
- SMTP_HOST
- SMTP_PORT
- SMTP_FROM_NAME
- SMTP_USERNAME
- SMTP_PASSWORD
- SMTP_SECURE=true
backend:
image: infisical/infisical:${INFISCAL_VERSION:-v0.63.1-postgres}
container_name: infisical-backend
restart: unless-stopped
pull_policy: always
ports:
- 80:8080
depends_on:
db:
condition: service_healthy
redis:
condition: service_started
db-migration:
condition: service_completed_successfully
environment:
- NODE_ENV=production
- ENCRYPTION_KEY
- AUTH_SECRET
- SITE_URL
- DB_CONNECTION_URI=postgres://${POSTGRES_USER}:${POSTGRES_PASSWORD}@db:5432/${POSTGRES_DB}
- REDIS_URL=redis://redis:6379
- SMTP_HOST
- SMTP_PORT
- SMTP_FROM_NAME
- SMTP_USERNAME
- SMTP_PASSWORD
- SMTP_SECURE=true
redis:
image: redis
container_name: infisical-dev-redis
restart: always
environment:
- ALLOW_EMPTY_PASSWORD=yes
volumes:
- redis_data:/data
db:
image: postgres:14-alpine
container_name: infisical-db
restart: always
volumes:
- pg_data:/var/lib/postgresql/data
healthcheck:
test: "pg_isready --username=${POSTGRES_USER} && psql --username=${POSTGRES_USER} --list"
interval: 5s
timeout: 10s
retries: 10
environment:
- POSTGRES_PASSWORD
- POSTGRES_USER
- POSTGRES_DB
volumes:
pg_data:
driver: local
redis_data:
driver: local
SMTP_SECURE which causes infisical to use STARTTLS if TLS connection not possible.
Create The Env File
COMPOSE_PROJECT_NAME=infiscal
# Specify the Docker image tag for the version of infiscal
# we wish to use.
# https://hub.docker.com/r/infisical/infisical/tags
INFISICAL_VERSION="v0.63.1-postgres"
# Required key for platform encryption/decryption ops
# Must be a random 16 byte hex string.
# Generate by executing: openssl rand -hex 16
ENCRYPTION_KEY=
# Required secret for signing JWT tokens
# Must be a random 32 byte base64 string
# Generate by executing: openssl rand -base64 32
AUTH_SECRET=
# Postgres credentials
# These don't necessarily need to change as the database
POSTGRES_USER=infisical
POSTGRES_DB=infisical
POSTGRES_PASSWORD=
# Website URL
# Required
SITE_URL=https://infisical.mydomain.com
# Mail/SMTP
# If using gmail, you would need to generate an app-specific password
# https://security.google.com/settings/security/apppasswords
SMTP_HOST=smtp.gmail.com
SMTP_PORT=587
SMTP_FROM_NAME=Infisical
SMTP_FROM_ADDRESS=username@gmail.com
SMTP_USERNAME=username@gmail.com
SMTP_PASSWORD=
Configure Reverse Proxy
For TLS certificate management, you need to configure a reverse proxy that will handle the certificates and terminate the TLS connection before passing plain HTTP traffic to your deployed infiscal container. You can do this either by deploying something like Nginx proxy manager, or I have the Nginx configuration that I used for my Debian nginx reverse proxy.
server {
listen 80;
server_name infisical.mydomain.com;
access_log /var/log/nginx/access.log;
location / {
return 302 https://$host$request_uri;
}
}
server {
listen 443 ssl;
server_name infisical.mydomain.com;
access_log /var/log/nginx/access.log;
error_log /var/log/nginx/error.log;
ssl_certificate /etc/nginx/ssl/infisical.mydomain.com/fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/infisical.mydomain.com/private.pem;
ssl_protocols TLSv1.3;
ssl_ciphers RC4:HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
keepalive_timeout 60;
ssl_session_cache shared:SSL:10m;
ssl_session_timeout 10m;
location / {
proxy_pass http://192.168.x.y/;
include /etc/nginx/proxy.conf;
}
}
FQDN from infiscal.mydomain.com, and also change http://192.168.x.y/ to make use of your infiscal server's internal/private IP address.
Register
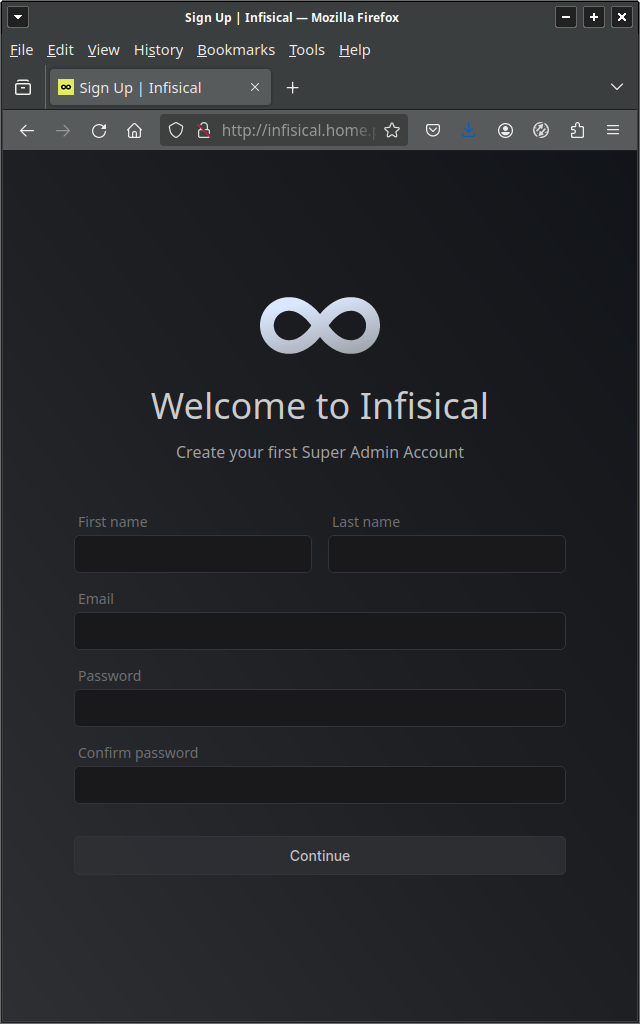
Navigate to the FQDN or IP address of your infiscal server and you should see the following screen. Fill it in to create the first user, the "Super Admin".
Disable User Registration
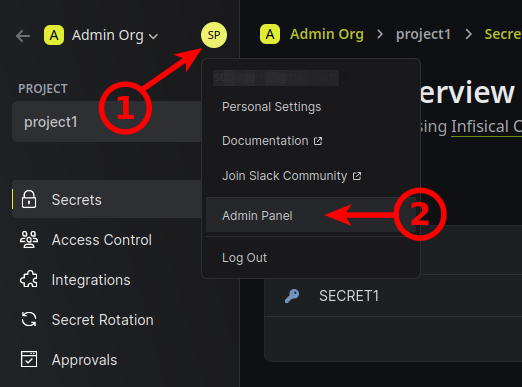
Users are allowed to register by default, so we probably want to disable this.
Click on your profile icon (1) to bring up the menu and click Admin Panel (2).
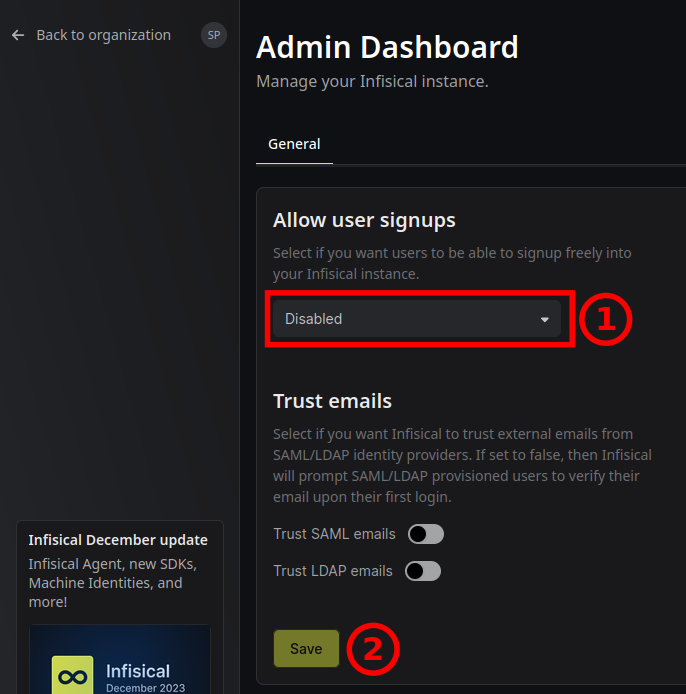
Under Allow user signups change the dropdown to Disabled.
Appendix
cURL Example
Below is an example for authenticating via cURL.
CLIENT_ID=
CLIENT_SECRET=
curl \
--location \
--request POST 'https://infisical.mydomain.com/api/v1/auth/universal-auth/login' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode "clientSecret=$CLIENT_SECRET" \
--data-urlencode "clientId=$CLIENT_ID"
GitLab Integration
Please refer to the native secrets integration documentation.
References
First published: 21st June 2024
