Nautilus GPG Integration
This tutorial will show Ubuntu users how to setup their file manager so that they can encrypt and decrypt files in future with GPG, without having to open up the terminal and manually encrypting/decrypting files.
Nautilus is the default filemanager in Ubuntu 14.04, which does not come with encryption integration in the context menu when
right-clicking files. One can add this by installing the seahorse-nautilus package.
sudo apt-get install seahorse-nautilus -y
One needs to restart nautilus for the changes to take effect.
killall nautilus
nautilus &
Now you should see the encrypt option in the context menu when right-clicking a file.
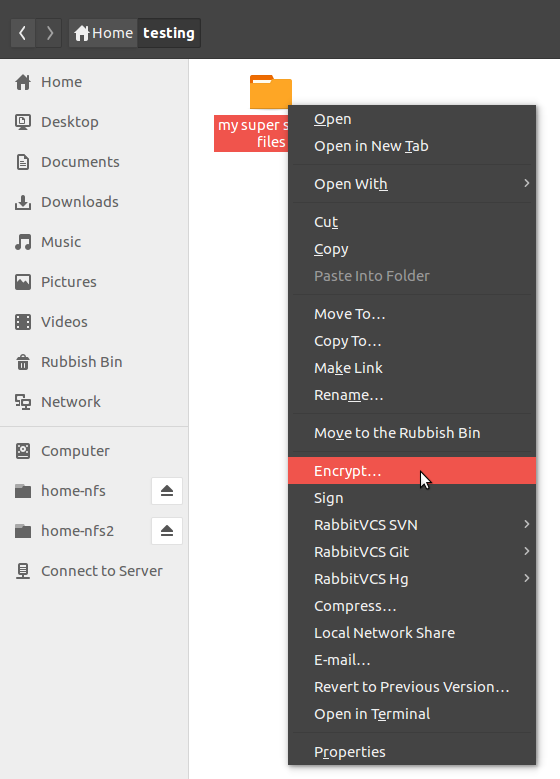
When you click on it for the first time, you will probably see the following popup. If you don't, then skip ahead.
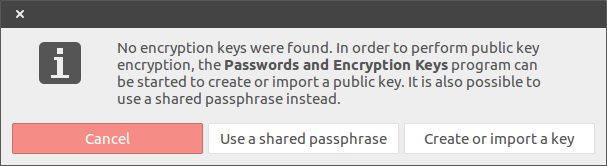
Click "create or import key" and the following window should appear:
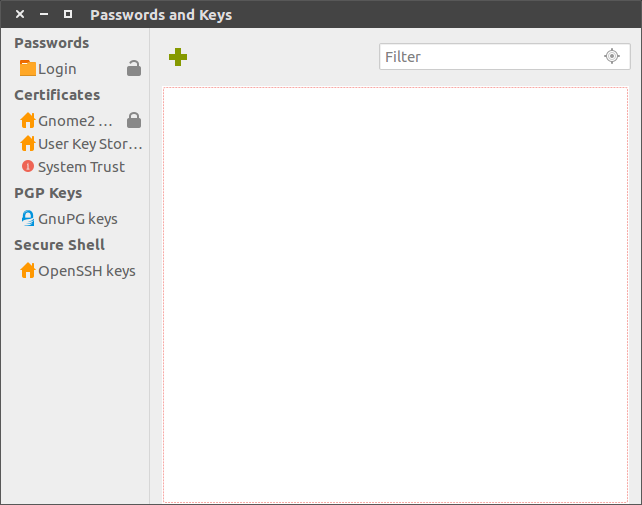
At this point, close the window and follow my tutorial on generating a GPG key through the CLI. This is because when I tried generating the GPG key through the GUI, I filled in all the dialogues and they disappeared with no result. I believe that it was working away in the background, waiting for me to interface with my computer to generate entropy, but the user never sees anything to let them know that it is actually doing anything, or given any kind of notice how far it is progressing.
Now open up nautilus and right click the file you wish to encrypt. Then click "create or import key" and click GnuPG keys. This time you should see your key to select from.
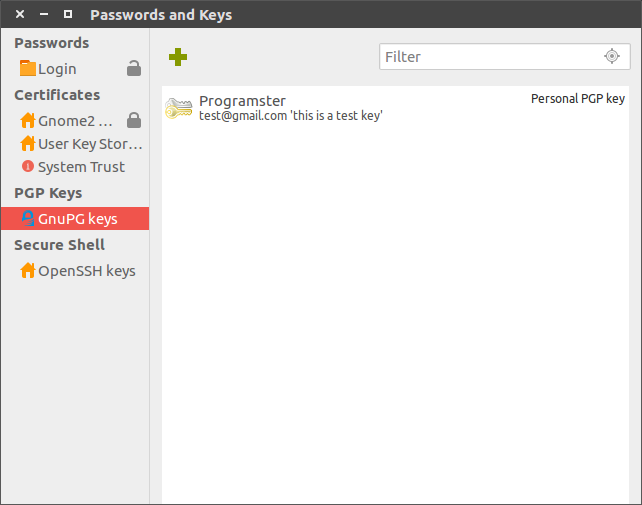
Select the key. You may choose to sign it which is not the default.

Your file should now appear with the .pgp extension in the same folder. The original file will remain after it has been decrypted. You probably want to delete it at this point.
Decrypting Files
You should be able to right-click your .pgp files and the top entry will be the option to decrypt the file.

After selecting to decrypt that option, you will be asked for your password for unlocking the PGP key. It appears that the program keeps the password in memory, because if you choose to decrypt the file again, you will not be asked for the password.
The original encrypted file will remain after decryption.
Exporting / Importing Keys
You can list keys by entering the command gpg --list-secret-keys. This will tell you the path to the keys and provide the comment you provided for each key, for if you have multiple keys.

To import the key into another computer, copy the key from the filepath to the other computer. Then import it with gpg --import [keyname].gpg. You can then list the secret keys to check that it was imported.
Key Storage
When making a backup of the key, do not post it publicly. Even though your key is password protected, your password will be far weaker to crack than the key. This means that your files are essentially ecrypted a key of roughly 128 bits or less instead of 2048 or more. Once someone has cracked your key, they can unlock your files, or worse, spread malicious content to others whilst pretending to be you. Do yourself a favour and buy a USB stick (or two) and stick all your sensitive keys and passwords on that. Alternatively, using a non rewriteable CD is slightly safer as you know the data could not have been changed once written.
Conclusion
You should now be able to encrypt and decrypt files conveniently in Nautilus.
First published: 16th August 2018
