AWS - Allow Servers To Communicate Across VPCs (VPC Peering)
Introduction
A Virtual private cloud (VPC) provides a level of sucurity through network isolation like your home NAT network. As long as your server's whitelist the CIDR of the VPC they are within, they will be able to communicate with each other over the internal network securely, whilst the public does not have access. However, if you have server's across different VPC's then you have two choices.
- Have the server's communicate with each other using their public IP's (if they have them).
- Set up VPC peering so that the two VPCs can have network traffic between the two.
This tutorial will show you how to perform the second option, adding a VPC peering connection between two VPCs which may or may not even be within the same account.
Caveats
This worked for me because the two VPCs I had used two different subnets in the same region. I don't think this will work if your VPC's have overlapping CIDRs, or are in different regions.
Steps
Create The Peering Connection
Search for "vpc" and go into the VPC area of the dashboard.
Click on Peering connections in the side panel.
Click on the Create peering connection button in the top-right corner.
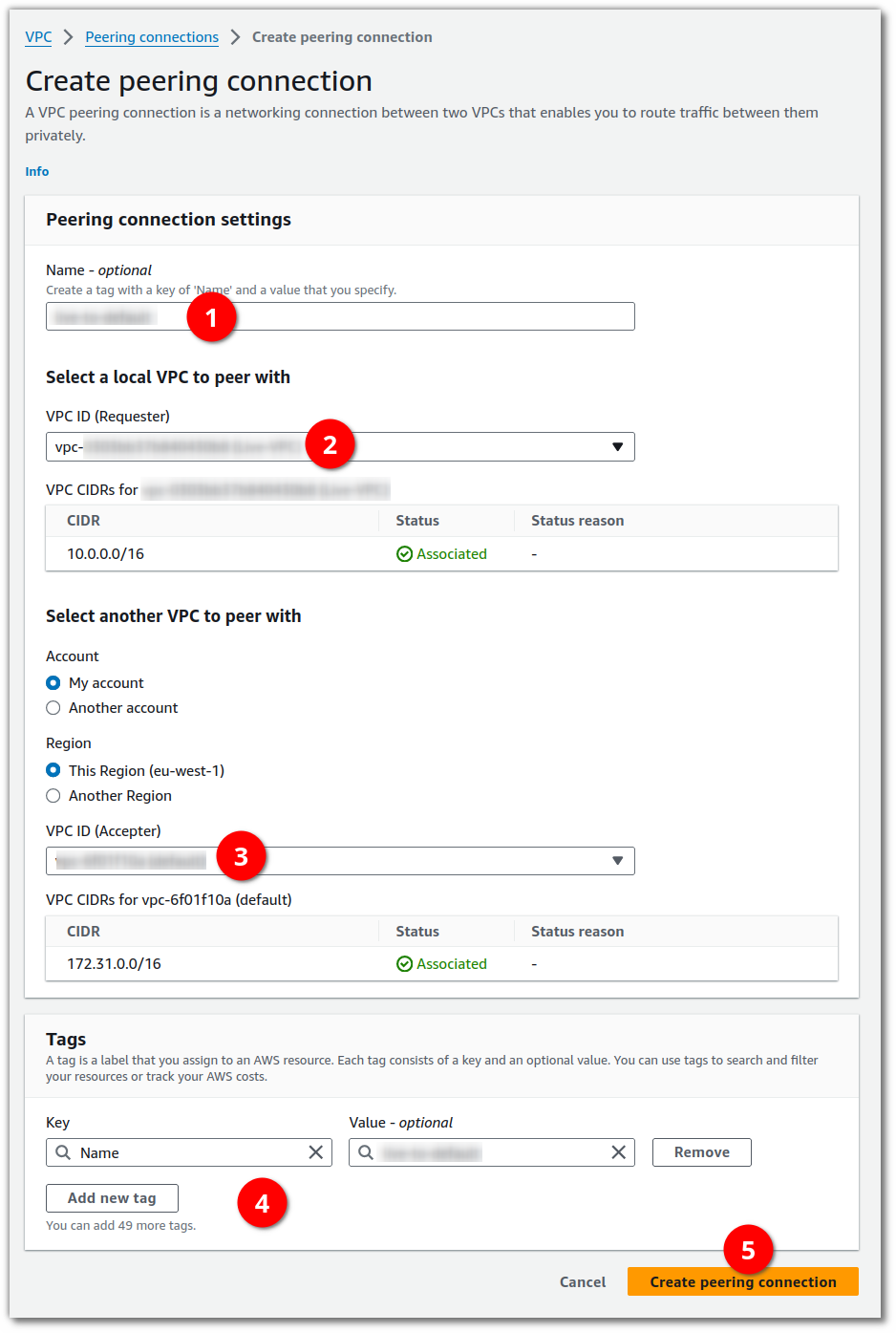
Fill in the form, giving this peering connection a name (1), selecting one of your VPCs that you wish to connect (2),
selecting the other VPC to connect with (3), possibly giving some additional tags (4), and clicking the button to create the connection (5).
After having created the peering connection, you will see that it is in a pending acceptance state (1).
Select the peering connection from the list (2), and click on the Actions button (3).
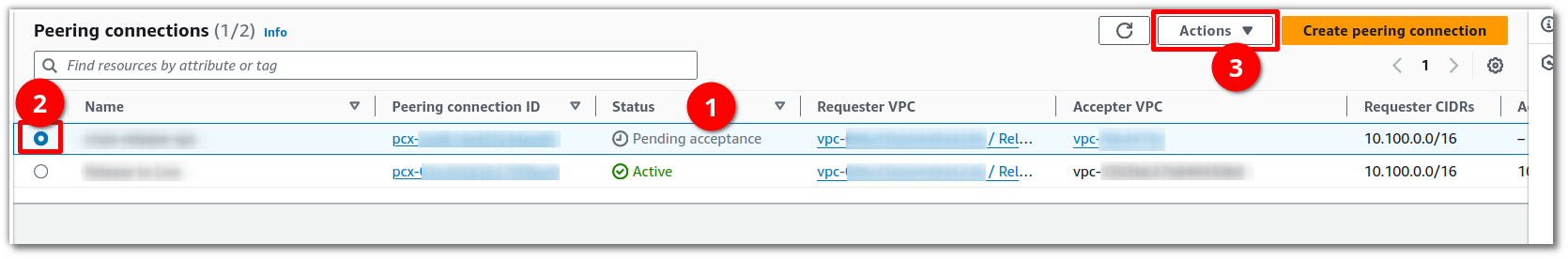
Click Accept Request.
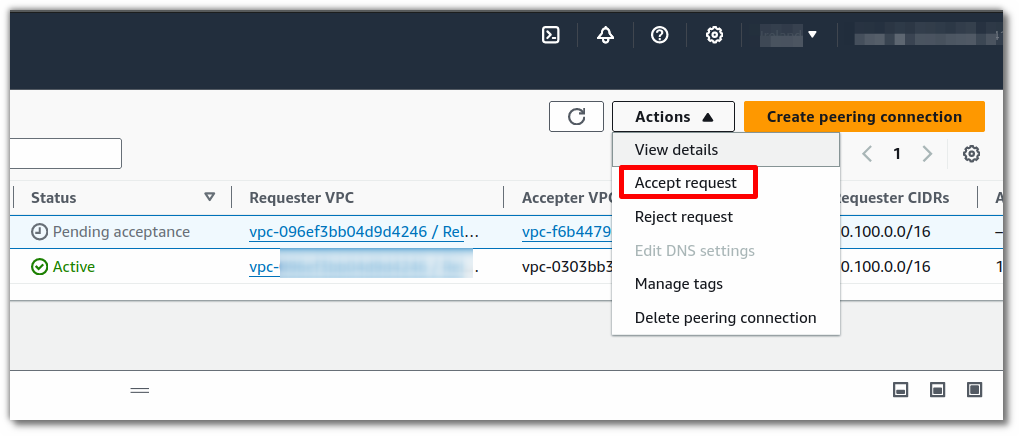
Review the details and press the button to accept the request in the modal that appears.
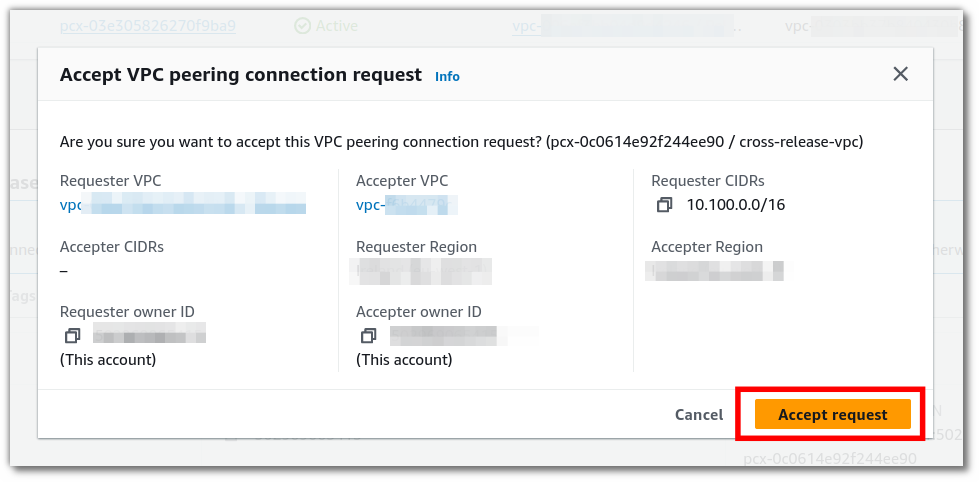
That's it. Your two VPCs are now able to communicate with each other.
Enabling DNS
By default, the VPC's will not resolve DNS queries to the internal/private IP of servers that are in the other VPC.
E.g. a DNS query for ec2-4-252-56-100.eu-west-1.compute.amazonaws.com would resolve to 4.252.56.100, instead of
something like 172.31.43.50.
If you wish to change it so that they do resolve to the internal IP, then follow these steps.
Select the peering connection you just created (or the one you need to fix DNS for) (1), and then click Actions.
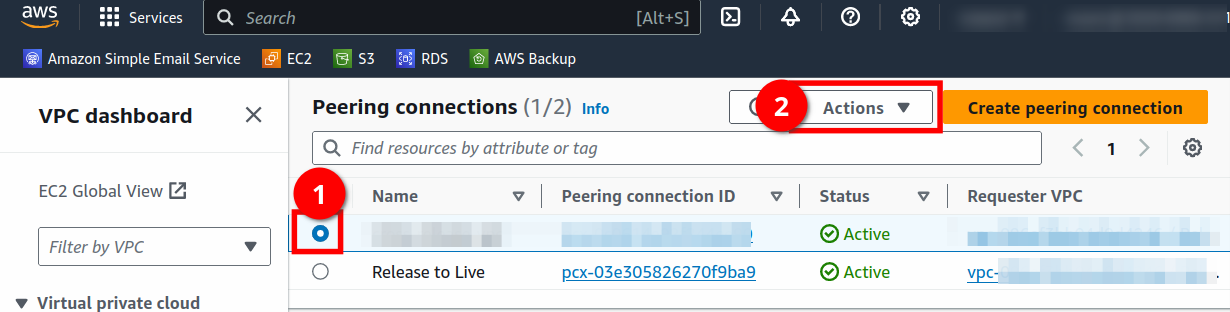
Select Edit DNS Settings.
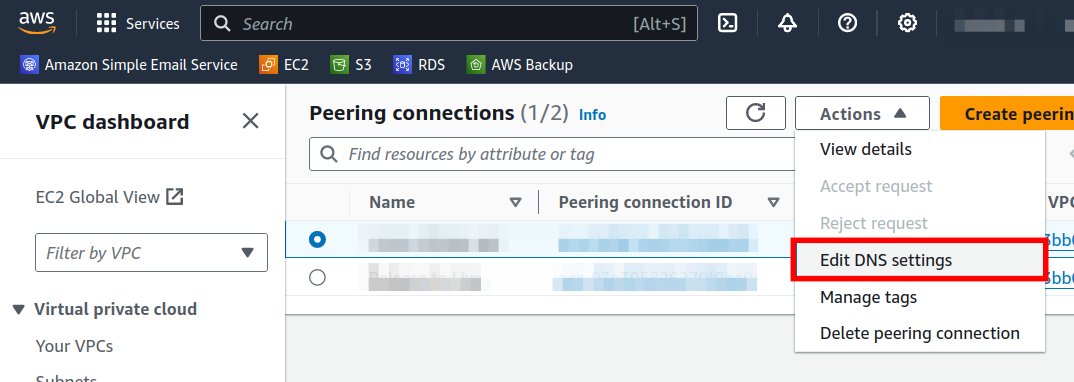
Check the checkboxes (1) for the DNS you wish to open up to the other VPC (you may wish for only one VPC to resolve the other, or you may wish for them to both work for each other). Then just save changes (2)

That's it! Now if you you use the EC2 CNAME record, such as:
ec2-52-214-102-220.eu-west-1.compute.amazonaws.com
... for one of your services in one of the VPCs, then the other VPC will resolve this to the internal IP, rather than that server's public IP, which has all of the relevant benefits in terms of security and network performance (make sure your security groups allow the internal IPs, and may not need to allow the public IPs.
Update Routing Tables
Now we need to update the routing tables of the subnets within our VPCs, so that they know that when a request comes in for an IP that is on the other VPC, that they should be routed through the peering connection. I was a little surprised that this was not automatically done for you since you cannot create peering connections between VPCs with overlapping subnets.
In your VPC dashboard, click on Subnets (1) to view the subnets across your VPCs. The VPC that each subnet belongs to will show in the table (2), along with the ipv4 (3) and IPv6 (4) CIDRs.
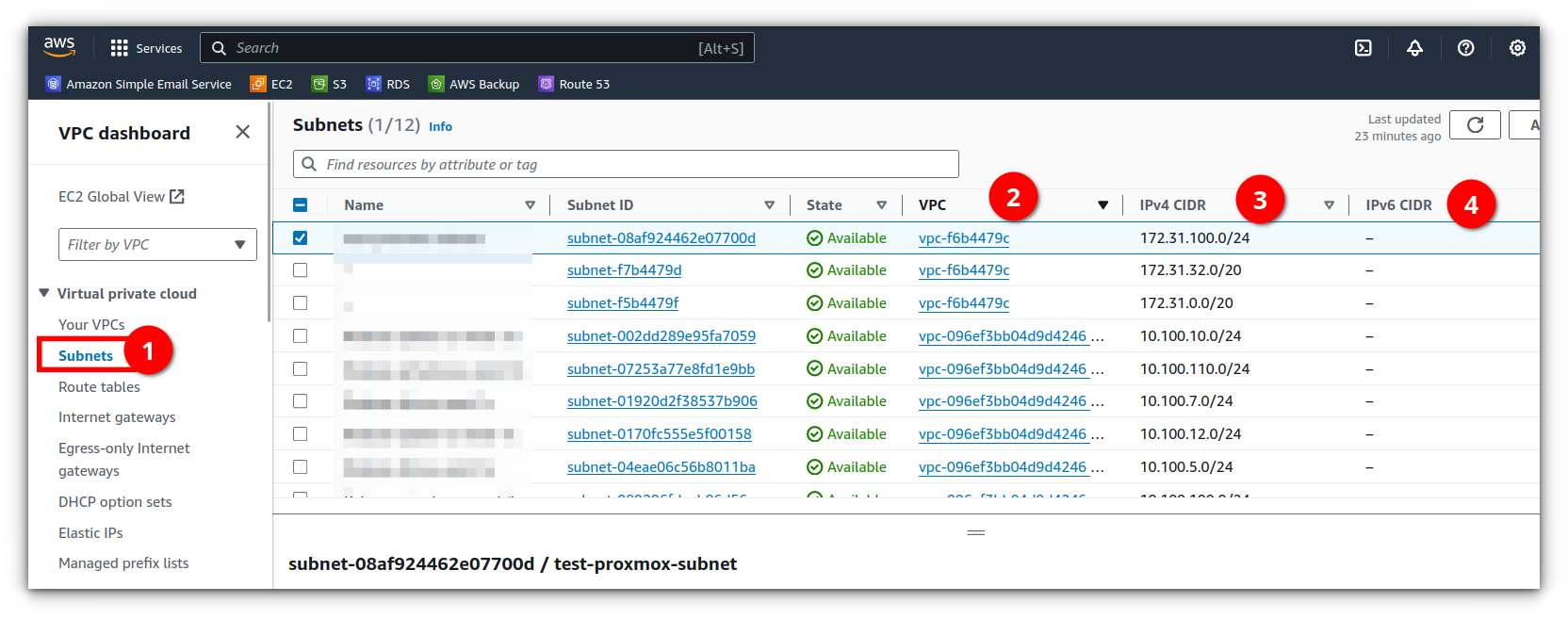
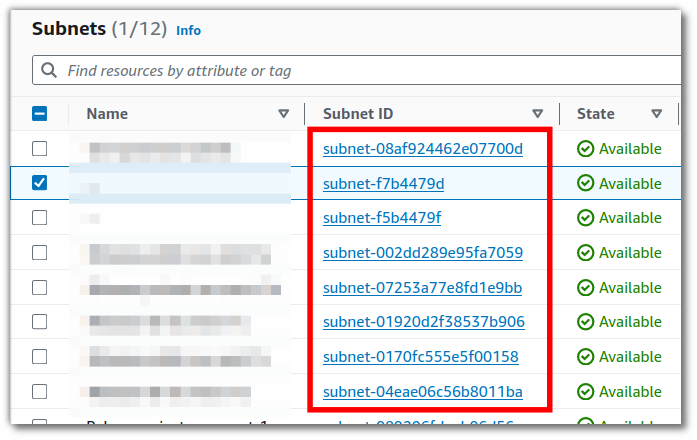
Click on the subnet ID of one of the subnets that belongs to one of the VPCs that you connected with the peering connection
You will be taken to a page showing the details of that subnet. Click on either of the links to the routing table to get to it.
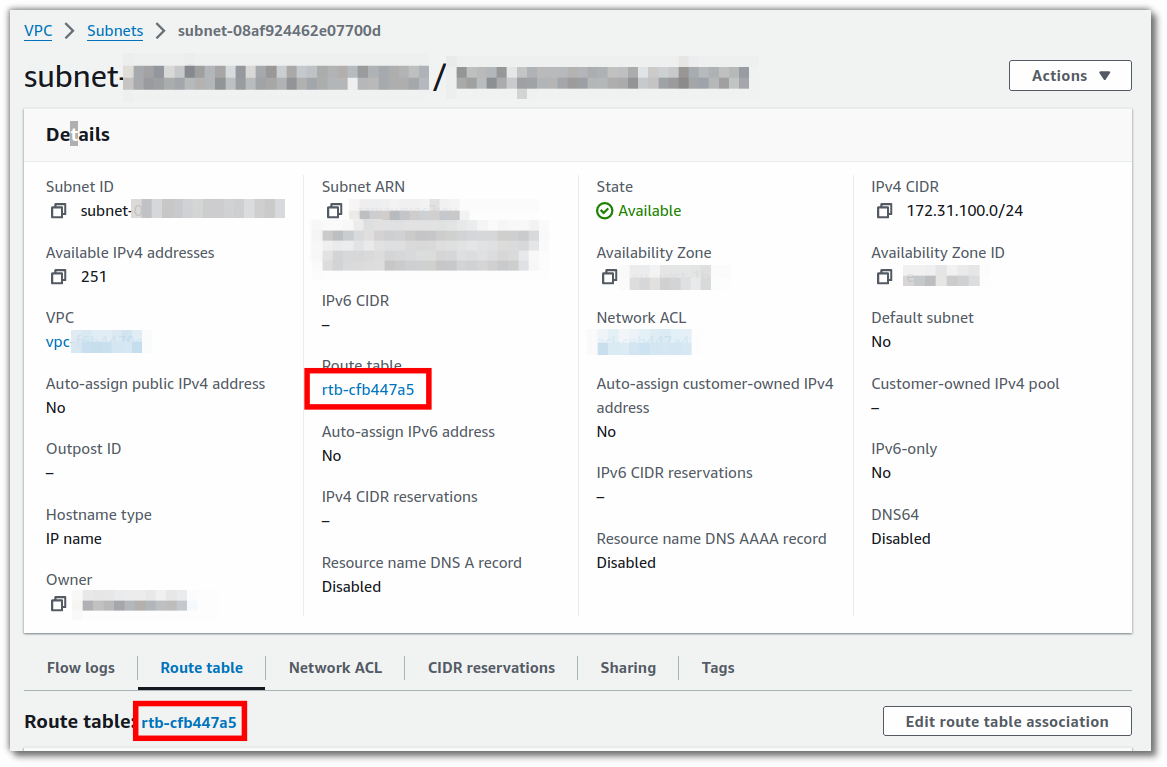
That will bring you to the route tables page, filtered to just that routing table. Click on its ID again.
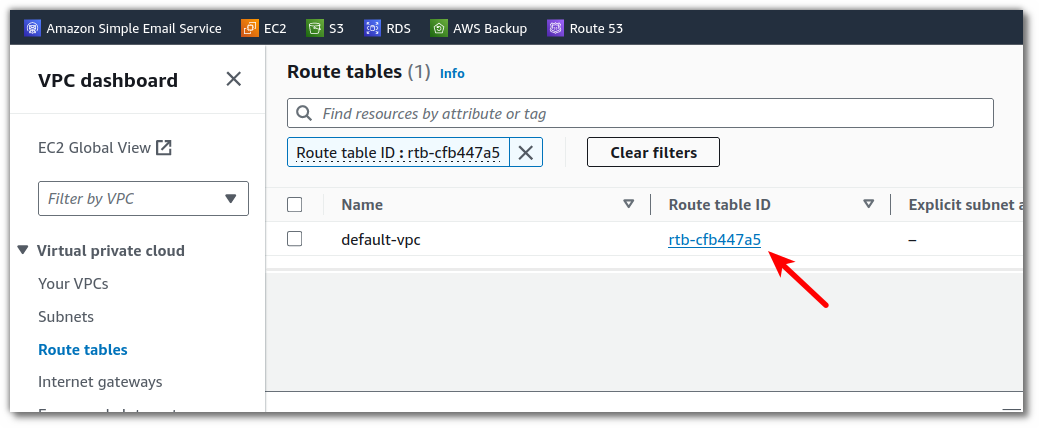
You will see the details of the routing table. Click Edit routes.
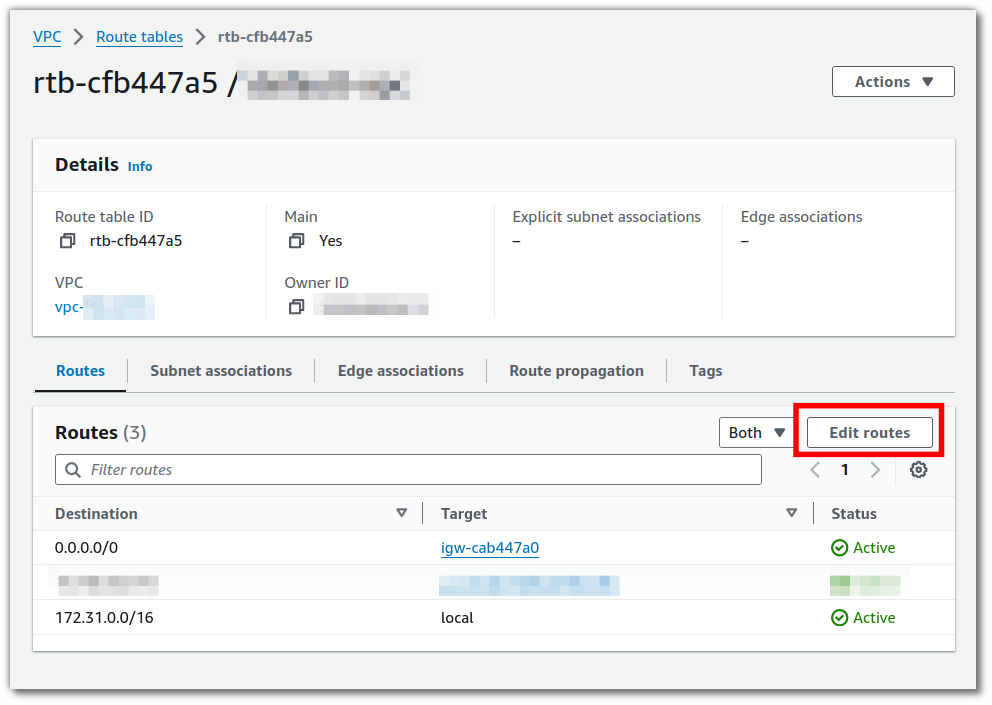
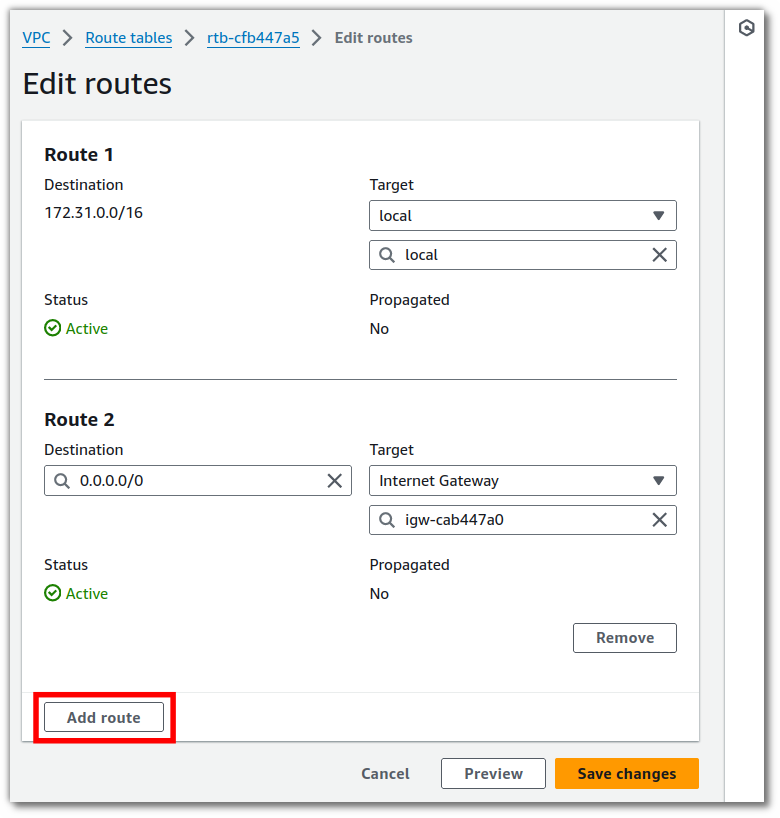
Click Add route.
Enter the CIDR of the other VPC that you peered with (1), and then select Peering connection and select the peering connection from the drop-down list (2). Then click save changes (3).
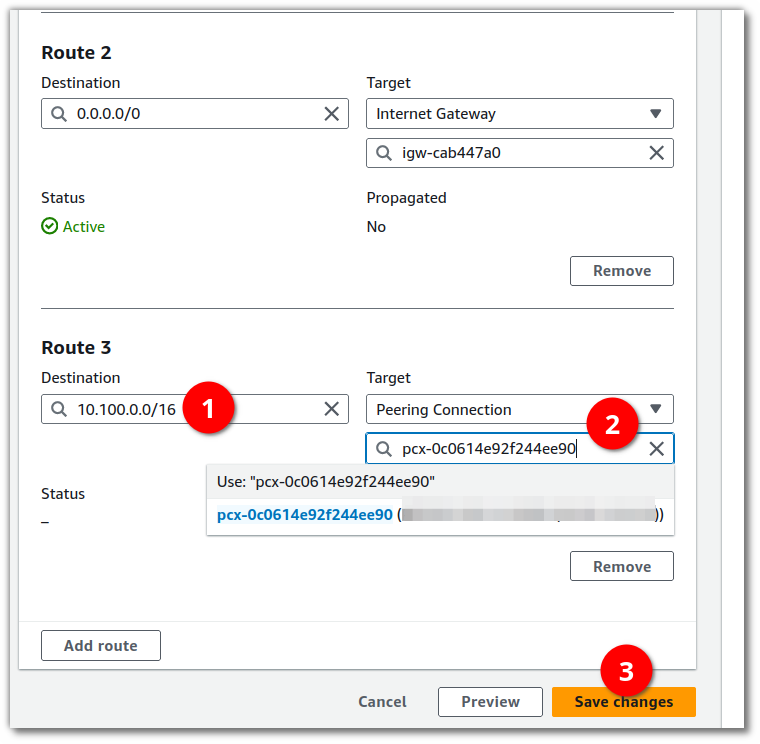
Repeat these steps for each of the routing tables in each of the subnets in your VPCs, so that both VPCs will route to the other over the peering connection. With very simple setups, there will be just one routing table for each VPC, so you will only have had to perform these steps twice, but don't forget that you need to specify the CIDR of the other VPC each time, so the inputs are not exactly the same.
Conclusion
That's it! You should now have network connectivity between the VPCs using the internal IP addresses. I would recommend testing this connectivity, and if anything is not working, then be sure to go back and check your subnet routing tables. The most common mistake will be having missed updating one or the routing tables, or having accidentaly plugged in the incorrect CIDR for specifying the other VPC that the subnet wishes to connect to.
First published: 9th July 2024
